Shirish Agarwal: Air Congestion and Politics
 Confession time first I am not a frequent flyer at all. My first flight was in early late 2006. It was a 2 hour flight from Bombay (BOM) to Bengaluru (formerly Bangalore, BLG) . I still remember the trepidation, the nervousness and excitement the first time I took to air. I still remember the flight very vividly,
It was a typical humid day for Bombay/Mumbai and we (me and a friend) had gone to Sahar (the domestic airport) to take the flight in the evening. Before starting the sky had turned golden-orange and I was wondering how I would feel once I would be in air.We started at around 20:00 hours in the evening and as it was a clear night were able to see the Queen s necklace (Marine Drive) in all her glory.
The photographs on the wikipedia page don t really do justice to how beautiful the whole boulevard looks at night, especially how it looks from up there. While we were seeing, it seemed the pilot had actually banked at 45 degrees angle so we can have the best view of the necklace OR maybe the pilot wanted to take a photo OR ME being in overdrive (like Robin Williams, the Russian immigrant in Moscow on the Hudson experiences the first time he goes to the mall ;))
In either way, this would be an experience I would never forget till the rest of my life. I remember I didn t move an inch (even to go the loo) as I didn t want to let go of the whole experience. While I came back after 3-4 days, I still remember re-experiencing/re-imagining the flights for a whole month each time I went to sleep.
While I can t say it has become routinised, but have been lucky to have the opportunity to fly domestic around the country primarily for work. After the initial romanticism wears off, you try and understand the various aspects of the flight which are happening around you.
These experiences are what lead to file/share today s blog post. Yesterday, Ms. Mamata Banerjee, one of the leaders of the Opposition cried wolf because the Aircraft was circling the Airport. Because she is the Chief Minister she feels she should have got precedent or at least that seems to be the way the story unfolded on TV.
I have been about 15-20 times on flight in the last decade for work or leisure. Almost all the flights I have been, it has been routine that the flights fly around the Airport for 15-20 minutes before landing. This is routine . I have seen Airlines being stacked (remember the scene from Die Hard 2 where Holly Mclane, John Mclane s wife looks at different aircraft at different altitudes from her window seat) this is what an Airport has to do when it doesn t have enough runaways. In fact just read few days back MIAL is going for an emergency expansion as they weren t expecting as many passengers as they did this year as well as last. In fact the same day there was a near-miss between two aircraft in Mumbai airport itself. Because of Ms. Mamata s belligerence, this story didn t even get a mention in the TV mainstream media.
The point I wanna underscore is that this is a fact of life and not just in India, world-over it seems hubs are being busier than ever, for instance Heathrow has been also a busy bee and they will to rework air operations as per a recent article .
In India, Kolkata is also one of the busier airports . If anything, I hope it teaches her the issues that plague most Indian airports and she works with the Government in Center so the Airport can expand more. They just got a new terminal three years back.
It is for these issues that the Indian Government has come with the Regional Connectivity Scheme .
Lastly, a bit of welcome news to people thinking to visit India, the Govt. of the day is facilitating easier visa norms to increase tourism and trade to India. Hope this is beneficial to all and any Debian Developers who wanna come visit India
Confession time first I am not a frequent flyer at all. My first flight was in early late 2006. It was a 2 hour flight from Bombay (BOM) to Bengaluru (formerly Bangalore, BLG) . I still remember the trepidation, the nervousness and excitement the first time I took to air. I still remember the flight very vividly,
It was a typical humid day for Bombay/Mumbai and we (me and a friend) had gone to Sahar (the domestic airport) to take the flight in the evening. Before starting the sky had turned golden-orange and I was wondering how I would feel once I would be in air.We started at around 20:00 hours in the evening and as it was a clear night were able to see the Queen s necklace (Marine Drive) in all her glory.
The photographs on the wikipedia page don t really do justice to how beautiful the whole boulevard looks at night, especially how it looks from up there. While we were seeing, it seemed the pilot had actually banked at 45 degrees angle so we can have the best view of the necklace OR maybe the pilot wanted to take a photo OR ME being in overdrive (like Robin Williams, the Russian immigrant in Moscow on the Hudson experiences the first time he goes to the mall ;))
In either way, this would be an experience I would never forget till the rest of my life. I remember I didn t move an inch (even to go the loo) as I didn t want to let go of the whole experience. While I came back after 3-4 days, I still remember re-experiencing/re-imagining the flights for a whole month each time I went to sleep.
While I can t say it has become routinised, but have been lucky to have the opportunity to fly domestic around the country primarily for work. After the initial romanticism wears off, you try and understand the various aspects of the flight which are happening around you.
These experiences are what lead to file/share today s blog post. Yesterday, Ms. Mamata Banerjee, one of the leaders of the Opposition cried wolf because the Aircraft was circling the Airport. Because she is the Chief Minister she feels she should have got precedent or at least that seems to be the way the story unfolded on TV.
I have been about 15-20 times on flight in the last decade for work or leisure. Almost all the flights I have been, it has been routine that the flights fly around the Airport for 15-20 minutes before landing. This is routine . I have seen Airlines being stacked (remember the scene from Die Hard 2 where Holly Mclane, John Mclane s wife looks at different aircraft at different altitudes from her window seat) this is what an Airport has to do when it doesn t have enough runaways. In fact just read few days back MIAL is going for an emergency expansion as they weren t expecting as many passengers as they did this year as well as last. In fact the same day there was a near-miss between two aircraft in Mumbai airport itself. Because of Ms. Mamata s belligerence, this story didn t even get a mention in the TV mainstream media.
The point I wanna underscore is that this is a fact of life and not just in India, world-over it seems hubs are being busier than ever, for instance Heathrow has been also a busy bee and they will to rework air operations as per a recent article .
In India, Kolkata is also one of the busier airports . If anything, I hope it teaches her the issues that plague most Indian airports and she works with the Government in Center so the Airport can expand more. They just got a new terminal three years back.
It is for these issues that the Indian Government has come with the Regional Connectivity Scheme .
Lastly, a bit of welcome news to people thinking to visit India, the Govt. of the day is facilitating easier visa norms to increase tourism and trade to India. Hope this is beneficial to all and any Debian Developers who wanna come visit India I do hope that we also do get reciprocity from those countries as well.
I do hope that we also do get reciprocity from those countries as well. Filed under: Miscellenous Tagged: # Domestic Flights, #Air Congestion, #Airport Expansion, #Kolkata, #near-miss, #Visa for tourists
 After upgrading an Ubuntu 14.04 ("trusty") machine to the latest 16.04
After upgrading an Ubuntu 14.04 ("trusty") machine to the latest 16.04

 Add the Ethereum APT repository using these commands:
Add the Ethereum APT repository using these commands:
 Julian has
Julian has
 Since moving to Japan, I got more and more interested in history, especially the recent history of the 20th century. The book I just finished, Ian Buruma (
Since moving to Japan, I got more and more interested in history, especially the recent history of the 20th century. The book I just finished, Ian Buruma ( The comparison of Germany and Japan with respect to their recent history as laid out in Buruma s book throws a spotlight on various aspects of the psychology of German and Japanese population, while at the same time not falling into the easy trap of explaining everything with difference in the guilt culture. A book of great depth and broad insights everyone having even the slightest interest in these topics should read.
The comparison of Germany and Japan with respect to their recent history as laid out in Buruma s book throws a spotlight on various aspects of the psychology of German and Japanese population, while at the same time not falling into the easy trap of explaining everything with difference in the guilt culture. A book of great depth and broad insights everyone having even the slightest interest in these topics should read.

 The
The 
 A friend and I regularly meet to chat over coffee and then usually finish up by walking the maintained trail in the
A friend and I regularly meet to chat over coffee and then usually finish up by walking the maintained trail in the 







 I recently obtained the newest Dell's Ubuntu developer offering, XPS 13 (2015, model 9343). I opted in for FullHD non-touch display, mostly because of better battery life, the actual no need for higher resolution, and matte screen which is great outside. Touch would have been "nice-to-have", but in my work I don't really need it.
I recently obtained the newest Dell's Ubuntu developer offering, XPS 13 (2015, model 9343). I opted in for FullHD non-touch display, mostly because of better battery life, the actual no need for higher resolution, and matte screen which is great outside. Touch would have been "nice-to-have", but in my work I don't really need it.



 Been writing photo viewer in nodejs.
I have a raspberrypi with 3TB HDD to archive camera photo data. It's not easy to retrieve data from it.
I tried running geeqie via ssh and it was slow waiting for it to repaint the display. shotwell seems to be too heavyweight.
I tried running sshfs and running geeqie but it was very slow waiting for IO to complete.
I tried implementing simple web service using nodejs that retrieves a day of photos, and it just crashed browser due to too much data, and the download size was huge.
I tried thumbnailing and added on-demand loading, and now browser was surviving better but raspberrypi was spending seconds converting photos to thumbnails.
I haven't solved my itch yet.
Been writing photo viewer in nodejs.
I have a raspberrypi with 3TB HDD to archive camera photo data. It's not easy to retrieve data from it.
I tried running geeqie via ssh and it was slow waiting for it to repaint the display. shotwell seems to be too heavyweight.
I tried running sshfs and running geeqie but it was very slow waiting for IO to complete.
I tried implementing simple web service using nodejs that retrieves a day of photos, and it just crashed browser due to too much data, and the download size was huge.
I tried thumbnailing and added on-demand loading, and now browser was surviving better but raspberrypi was spending seconds converting photos to thumbnails.
I haven't solved my itch yet.

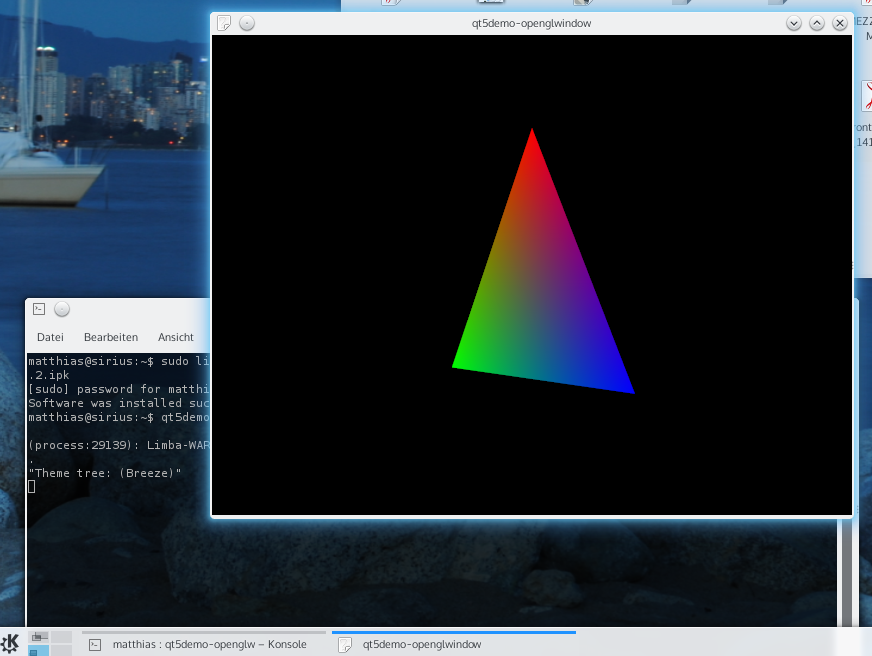
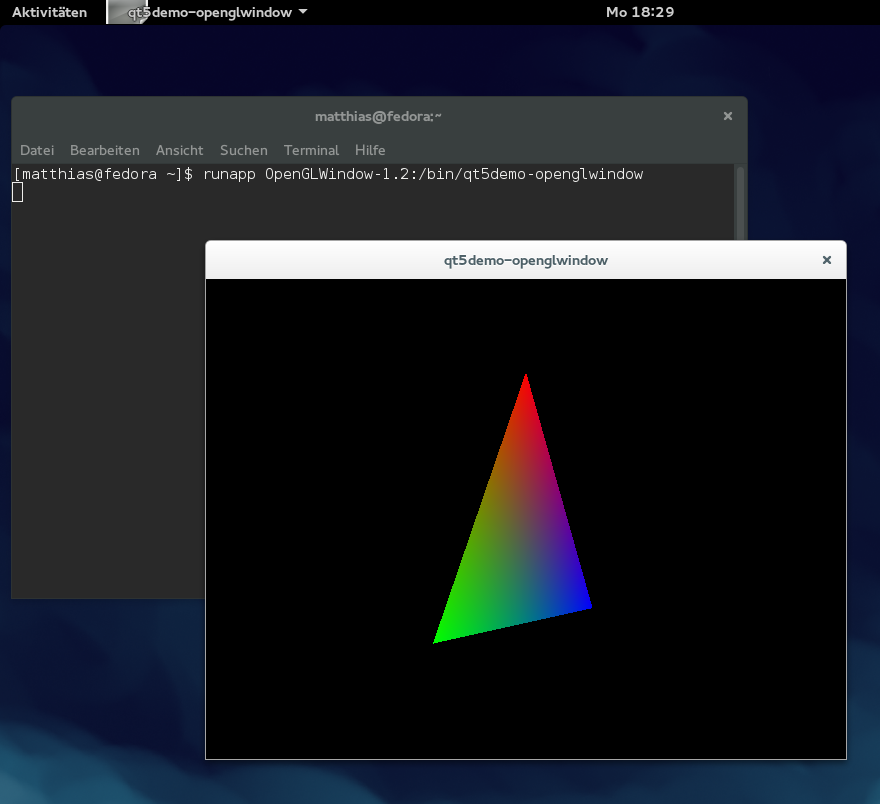
 I ve many distributed Linux instances across several clouds, be them global, such as
I ve many distributed Linux instances across several clouds, be them global, such as